This post will guide you how to install ArgoCD on the kubernetes, along with ingress access and intergrate with third parth authorization.
What is ArgoCD
Argo CD is a declarative, GitOps continuous delivery tool for Kubernetes.
Install
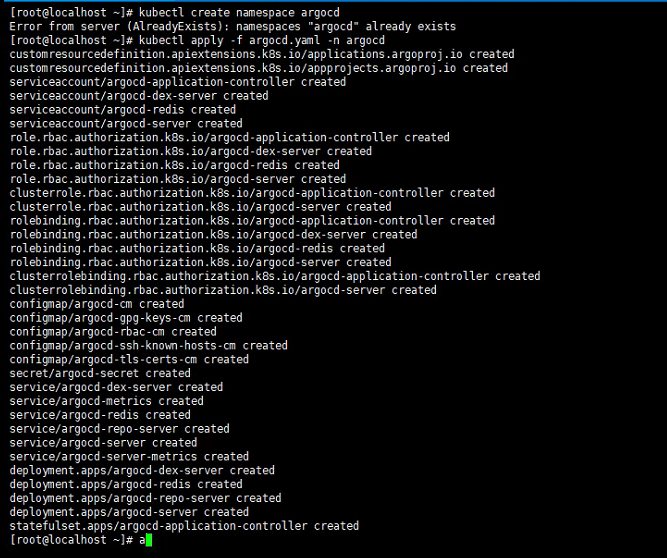
kubectl create namespace argocd
kubectl apply -n argocd -f https://raw.githubusercontent.com/argoproj/argo-cd/stable/manifests/install.yaml
Configure HTTP/HTTPS ingress for UI
Replace the value of host to a new value.
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: argocd-server-http-ingress
namespace: argocd
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
nginx.ingress.kubernetes.io/backend-protocol: "HTTP"
spec:
rules:
- http:
paths:
- backend:
serviceName: argocd-server
servicePort: http
host: argocd.example.com
tls:
- hosts:
- argocd.gosysops.com
secretName: argocd-secret # do not change, this is provided by Argo CD
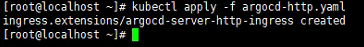
apply the HTTP yaml file
kubectl apply -f argocd-http.yaml
Configure GRPC ingress for client CLI access
same above, you need to change the value of host field.
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: argocd-server-grpc-ingress
namespace: argocd
annotations:
kubernetes.io/ingress.class: "nginx"
nginx.ingress.kubernetes.io/backend-protocol: "GRPC"
spec:
rules:
- http:
paths:
- backend:
serviceName: argocd-server
servicePort: https
host: grpc.argocd.example.com
tls:
- hosts:
- grpc.argocd.gosysops.com
secretName: argocd-secret # do not change, this is provided by Argo CD
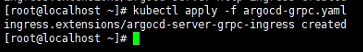
apply grpc ingress
kubectl apply argocd-grpc.yaml
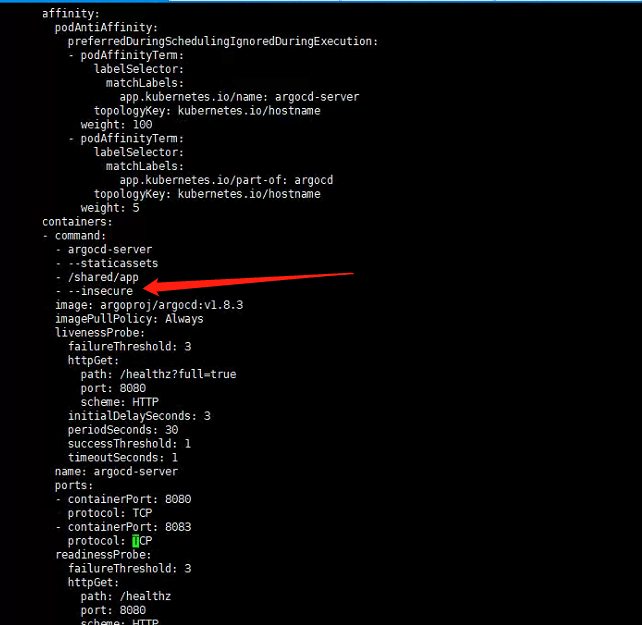
Configure argo-server to allow HTTP
edit argo-server deoployment to add parameters
Default Password
For ArgoCD 1.8, the initial password is autogenerated to be the pod name of the ArgoCD API server. This can be retrieved with the command:
kubectl get pods -n argocd -l app.kubernetes.io/name=argocd-server -o name | cut -d'/' -f 2
it won’t be work sometimes, you can re-deployment argocd-server. but the simplest way is to change password with updating config map.
go to the https://www.browserling.com/tools/bcrypt to generate a new hash password.
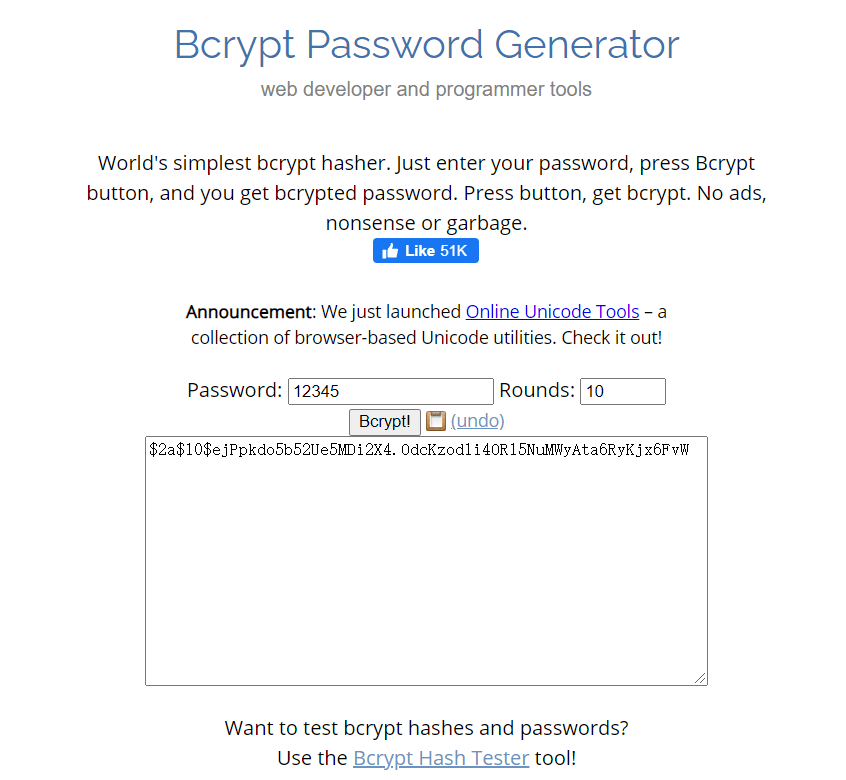
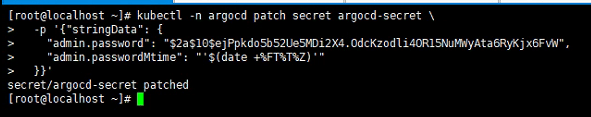
replace the value of admin.password field and apply it
kubectl -n argocd patch secret argocd-secret \
-p '{"stringData": {
"admin.password": "$2a$10$ejPpkdo5b52Ue5MDi2X4.OdcKzodli4OR15NuMWyAta6RyKjx6FvW",
"admin.passwordMtime": "'$(date +%FT%T%Z)'"
}}'
Login