if you’ve read the news recently, you must hear about the Log4Shell zero-day in log4j, this vulnerability affects at least millions of computer, system, and java applications. I won’t elaborate details here, for more information about this, you can check out from here.
In this article, I will be talking about how to add kong plugins to mitigate log4shell attacks, an engineer at Kong has developed a plugin to mitigate attacks. Kong said their kong products are not affected by log4shell.
Prepare
Download the below files to local. Kong Dockerfile will be used to build a new image, Kong Log4shell is a Kong plugin, and Luarocks is used to install plugin to Kong.
The image will be based on centos 8, plugin tar file, lurocks, lurocks-admin and kong configuration file are needed to place docker-kong/centos/ directory.
Enable Kong Plugin
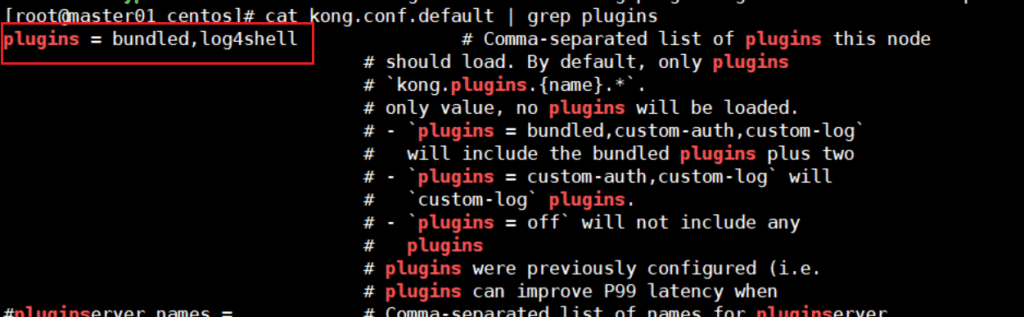
To make kong aware that it has to look for our plugin, we need to add it to the plugins property in the configuration file, which is separated by a comma.
Update Dockerfile
I’ve updated official Dockerfile by copying luarocks, kong configuration, installing the kong plugin, and setting up permission.
FROM centos:8
LABEL maintainer="Kong <support@konghq.com>"
ARG ASSET=ce
ENV ASSET $ASSET
ARG EE_PORTS
COPY kong.rpm /tmp/kong.rpm
COPY ./luarocks /usr/bin/
COPY ./luarocks-admin /usr/bin/
COPY ./kong-plugin-log4shell.tar.gz /
COPY ./kong.conf.default /etc/kong/kong.conf
ARG KONG_VERSION=2.7.0
ENV KONG_VERSION $KONG_VERSION
ARG KONG_SHA256="d69aedffbecf697482f7ef3f9ea8087e6487702e1683732205aaed108adb0c3d"
# hadolint ignore=DL3033
RUN set -ex; \
if [ "$ASSET" = "ce" ] ; then \
curl -fL https://download.konghq.com/gateway-${KONG_VERSION%%.*}.x-centos-8/Packages/k/kong-$KONG_VERSION.el8.amd64.rpm -o /tmp/kong.rpm \
&& echo "$KONG_SHA256 /tmp/kong.rpm" | sha256sum -c -; \
else \
# this needs to stay inside this "else" block so that it does not become part of the "official images" builds (https://github.com/docker-library/official-images/pull/11532#issuecomment-996219700)
yum update -y \
&& yum upgrade -y ; \
fi; \
yum install -y -q unzip shadow-utils git \
&& yum clean all -q \
&& rm -fr /var/cache/yum/* /tmp/yum_save*.yumtx /root/.pki \
# Please update the centos install docs if the below line is changed so that
# end users can properly install Kong along with its required dependencies
# and that our CI does not diverge from our docs.
&& yum install -y /tmp/kong.rpm \
&& yum clean all \
&& rm /tmp/kong.rpm \
&& chown kong:0 /usr/local/bin/kong \
&& chown -R kong:0 /usr/local/kong \
&& ln -s /usr/local/openresty/bin/resty /usr/local/bin/resty \
&& ln -s /usr/local/openresty/luajit/bin/luajit /usr/local/bin/luajit \
&& ln -s /usr/local/openresty/luajit/bin/luajit /usr/local/bin/lua \
&& ln -s /usr/local/openresty/nginx/sbin/nginx /usr/local/bin/nginx \
&& tar zxvf /kong-plugin-log4shell.tar.gz\
&& cd /kong-plugin-log4shell \
&& luarocks make \
&& chown kong:kong /usr/local/share/lua/5.1/kong/plugins/log4shell \
&& if [ "$ASSET" = "ce" ] ; then \
kong version; \
fi
COPY docker-entrypoint.sh /docker-entrypoint.sh
USER kong
ENTRYPOINT ["/docker-entrypoint.sh"]
EXPOSE 8000 8443 8001 8444 $EE_PORTS
STOPSIGNAL SIGQUIT
HEALTHCHECK --interval=10s --timeout=10s --retries=10 CMD kong health
CMD ["kong", "docker-start"]Verify plugins
To make sure plugin is being loaded by Kong, we can start Kong with a debug log level:
docker run -it --rm --name kong -e "KONG_DATABASE=off" -e "KONG_PROXY_ACCESS_LOG=/dev/stdout" -e "KONG_ADMIN_ACCESS_LOG=/dev/stdout" -e "KONG_PROXY_ERROR_LOG=/dev/stderr" -e "KONG_ADMIN_ERROR_LOG=/dev/stderr" -e "KONG_LOG_LEVEL=debug" kong:2.7.0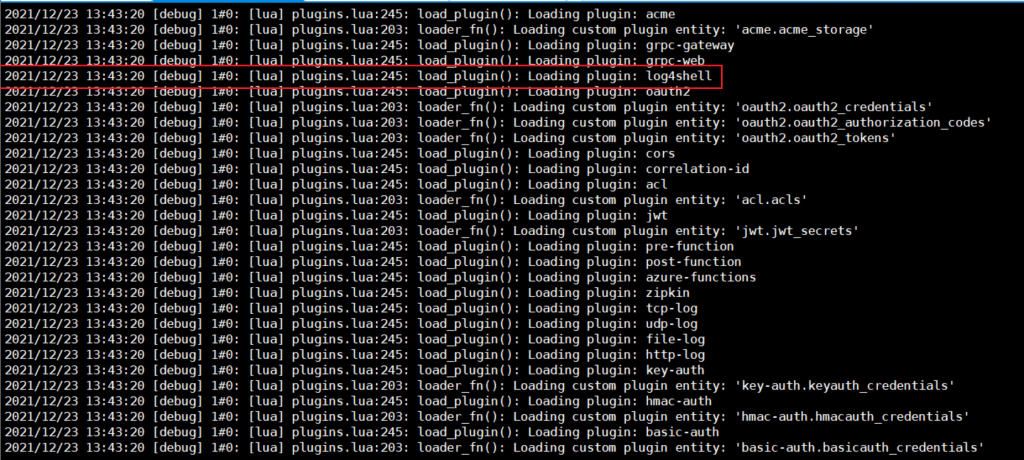
Conclusion
To wrap this up, let’s recap what we’ve learned in this post.
- Log4Shell is a remote code execution vulnerability in Log4J, a popular Java logging library
- No Kong products are affected by log4shell
- Kong-plugin-log4shell plugin can mitigate log4shell attack.
Reference
Log4J, Log4Shell and Kong – KongHQ
Plugin Development – (un)Installing your plugin – v2.7.x | Kong Docs (konghq.com)